Every System Has Vulnerabilities – Do You Know Where Yours Are?
 It is important to identify the vulnerabilities in your system and ensure remedial action to prevent security breaches and data loss. Weak spots are prime targets for threat actors. Providing opportunities for them to steal sensitive data and cause damage to your network, or deny access to authorized users.
It is important to identify the vulnerabilities in your system and ensure remedial action to prevent security breaches and data loss. Weak spots are prime targets for threat actors. Providing opportunities for them to steal sensitive data and cause damage to your network, or deny access to authorized users.
Vulnerability Management can help mitigate risks and improve your security posture. An effective operational risk management framework includes regularly reviewed and updated policies and procedures, a risk classification system that includes categories of risks related to people, inadequate internal processes and systems, and external events, and assessment and monitoring tools to evaluate risks and controls.
From an organizational standpoint, operational risk management requires several collaborative defensive systems to properly assess and manage risk, including vulnerability scanning, user validation, and threat
 Identify & Manage Risk
Identify & Manage Risk
Operational risk management is centered on the assurance that all vulnerabilities associated with business activities are properly identified and understood, that the associated risks are formally assessed and quantified, and that there is a structured process in place for enacting the decisions made by leadership functions to manage vulnerabilities and the associated risks.
There are multiple regulatory frameworks focused on digital operational resilience and risk management. Organizations must now prove their Digital Operational Resilience. ICT risk management is a key pillar of these frameworks. A comprehensive risk management framework for ICT systems includes policies, procedures, regular assessments and programs.
Ensuring users can perform their routine tasks without reducing efficiency and effectiveness, while keeping systems and data secure and compliant, is the key to managing risk effectively.
How can Monitoring Nonstop-Connected Hardware Devices Strengthen Digital Operational Resilience?
Monitoring hardware devices is crucial for minimizing system downtime and ensuring optimal performance, efficiency, and security. It can provide real-time insights into hardware health, detect issues before they escalate, prevent data loss, and inform proactive maintenance and upgrade decisions.
Monitoring also improves insight and visibility into the Hardware Security Module (HSM), facilitating more effective management and troubleshooting of any issues.
Regulatory compliance is no small undertaking. It requires the right partner to ensure not only compliance but also an environment of readiness and continuous improvement.
How can you Effectively Monitor Nonstop-Connected Hardware Devices?
CSP has been an innovator in NonStop security for over thirty years and understands the complex security challenges facing the NonStop platform.
No organization is immune to threats. CSP understands enterprises require insight and visibility into the Hardware Security module, so we developed CSP Syslog Receiver to assist with monitoring of devices connected to Nonstop environment.
CSP Syslog Receiver for Nonstop servers is an OSS Gateway tool that receives syslog messages from Hardware Security Modules (via TCP/IP or UDP), and forwards to EMS collectors. This solution delivers improved insight and visibility into the Hardware Security module (HSM), facilitating more effective management and troubleshooting.
The installation and setup are very quick, and the product is simple to use.
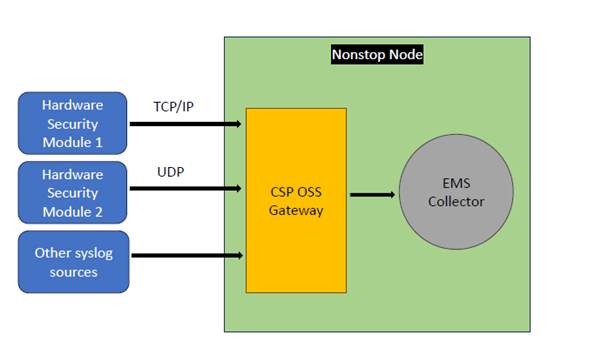
Supports Multiple Syslog Sources
In addition to Hardware Security Modules, messages from various other syslog sources can be sent to EMS, providing increased visibility and awareness of the devices connected to Nonstop environment.
CSP Syslog Receiver improves insight into the Hardware Security Module, increases visibility and awareness of devices connected to the Nonstop environment, and can receive critical messages regarding hardware failure/power failure. CSP Syslog Receiver now also supports Enterprise Security Key Managers (ESKM’s).
Key Features:
- OSS process managed by config file (YAML format)
- Supports TCP/IP and UDP protocols
- Supports multiple syslog sources
- Support for Enterprise Security Key Managers
- Ability to specify a dedicated EMS collector for Syslog messages
- Ability to run as a Pathway process
- Quick installation and setup
- Simple to use
- No GUI to install
When it comes to securing your NonStop Systems, you have options.
CSP – The Superior Choice in NonStop Security
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit wiki.cspsecurity.com
We Built the Wiki for NonStop Security ®
+1(905) 568 –8900












